If your computer doesn't recognize your connected device, you might see an unknown error or a '0xE' error. If you do, follow these steps and try to connect your device again after each step:
- Make sure that your iOS or iPadOS device is unlocked and on the Home screen.
- Check that you have the latest software on your Mac or Windows PC. If you're using iTunes, make sure you have the latest version.
- Make sure that your device is turned on.
- If you see a Trust this Computer alert, unlock your device and tap Trust.
- Unplug all USB accessories from your computer except for your device. Try each USB port to see if one works. Then try a different Apple USB cable.*
- Restart your computer.
- Restart your device:
- Try connecting your device to another computer. If you have the same issue on another computer, contact Apple Support.
NVIDIA® Driver - Security Vulnerability End of support notification for products using the Windows XP operating system Free Repair Program for VAIO Fit 11A/Flip Personal Computer. Working with IT – One of the more unexpected concerns I hear from OT teams is around how to work with IT to solve the security threats discussed above, when IT teams generally have little experience with industrial systems and their traditional security solutions typically aren’t compatible with legacy control systems. While many on the OT.

For more help, follow the steps below for your Mac or Windows PC.
* Learn how to connect iPad Pro (11-inch) or iPad Pro 12.9-inch (3rd generation) to your computer.
If you use a Mac
- Connect your iOS or iPadOS device and make sure that it's unlocked and on the Home screen.
- On your Mac, hold down the Option key, click the Apple menu, and choose System Information or System Report.
- From the list on the left, select USB.
- If you see your iPhone, iPad, or iPod under USB Device Tree, get the latest macOS or install the latest updates. If you don't see your device or still need help, contact Apple Support.
If you use a Windows PC
The steps differ depending on if you downloaded iTunes from the Microsoft Store or from Apple.
If you downloaded iTunes from the Microsoft Store
Ot Solutions Laptops For Gaming
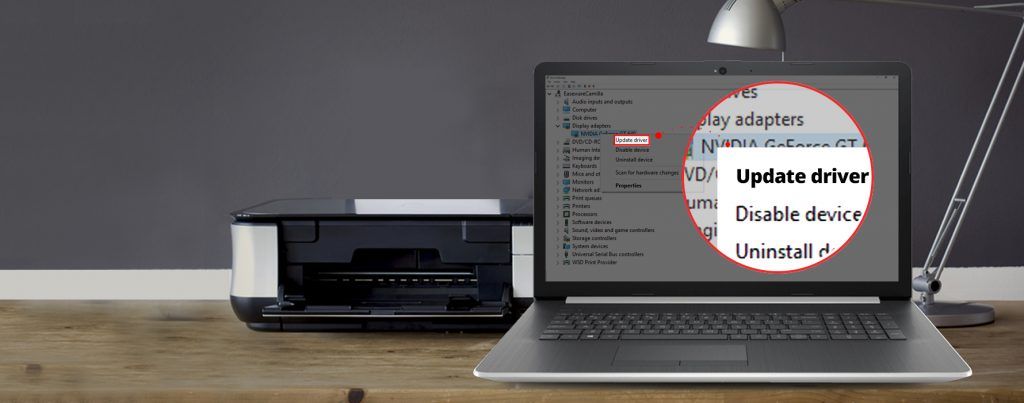
Follow these steps to reinstall the Apple Mobile Device USB driver:
- Disconnect your device from your computer.
- Unlock your iOS or iPadOS device and go to the Home screen. Then reconnect your device. If iTunes opens, close it.
- Click and hold (or right-click) the Start button, then choose Device Manager.
- Locate and expand the Portable Devices section.
- Look for your connected device (such as Apple iPhone), then right-click on the device name and choose Update driver.
- Select 'Search automatically for updated driver software.'
- After the software installs, go to Settings > Update & Security > Windows Update and verify that no other updates are available.
- Open iTunes.
If you downloaded iTunes from Apple
Follow these steps to reinstall the Apple Mobile Device USB driver:

- Disconnect your device from your computer.
- Unlock your iOS or iPadOS device and go to the Home screen. Then reconnect your device. If iTunes opens, close it.
- Press the Windows and R key on your keyboard to open the Run command.
- In the Run window, enter:
%ProgramFiles%Common FilesAppleMobile Device SupportDrivers - Click OK.
- Right-click on the
usbaapl64.inforusbaapl.inffile and choose Install.
You might see other files that start withusbaapl64orusbaapl. Make sure to install the file that ends in .inf. If you’re not sure which file to install, right-click a blank area in the File Explorer Window, click View, then click Details to find the correct file type. You want to install the Setup Information file. - Disconnect your device from your computer, then restart your computer.
- Reconnect your device and open iTunes.
If your device still isn't recognized
Check Device Manager to see if the Apple Mobile Device USB driver is installed. Follow these steps to open Device Manager:
- Press the Windows and R key on your keyboard to open the Run command.
- In the Run window, enter
devmgmt.msc, then click OK. Device Manager should open. - Locate and expand the Universal Serial Bus controllers section.
- Look for the Apple Mobile Device USB driver.
If you don't see the Apple Mobile Device USB Driver or you see Unknown Device:
- Connect your device to your computer with a different USB cable.
- Connect your device to a different computer. If you have the same issue on another computer, contact Apple Support.
If you see the Apple Mobile Device USB driver with an error symbol:
If you see , , or next to the Apple Mobile Device USB driver, follow these steps:
- Restart the Apple Mobile Device Service.
- Check for and resolve issues with third-party security software, then restart your computer.
- Try to install the
usbaapl64.inforusbaapl.inffile again.
10 Jan 2021 Unidirectional OT Zero Trust
Zero trust is a new way of thinking about cybersecurity for connected systems. Let’s explore what zero trust means for industrial/ICS/OT networks. New blog post by Blase Janov, Director of Business Development at Waterfall Security Solutions
Zero trust means computers and software systems no longer decide how much they trust each other simply because of their IP addresses. Instead, all connections between systems must be encrypted and authenticated. For example – consider a “road warrior” with a laptop in a hotel room. Many such laptops have no VPN connections any longer – they interact exclusively with cloud services and websites, using the HTTPS protocol. Every access from the laptop to such services is with a username, password, and possibly other bits of authentication. Any peer-to-peer connection between this laptop and, say, another laptop that a colleague is using in another city, is via intermediaries such as Zoom or Teamviewer, that arrange a rendezvous for the two laptops. The laptop is a classic zero-trust system – it cannot afford to trust anything it tries to connect to.
Industrial Internet
This very concept is the foundation of some definitions of the Industrial Internet of Things (IIoT). Edge devices (computers) are physically connected to some physical process to monitor and/or control physical operations. These edge devices are designed and hardened to be deployed on the open Internet. They connect to cloud services – generally the device vendor’s services – via HTTPS. All rendezvous between devices or between the devices and other cloud services are arranged via the vendor’s cloud service.
One vision for zero trust in the industrial Internet is that everything is either an edge devices or cloud service. For example, a power plant’s operator’s HMI, historian, alarm server and other servers would all be cloud services. PLCs would become edge devices, connecting across the Internet to the cloud services, or to their vendor’s cloud services. The PLCs would identify themselves with public key certificates. Systems integrators would configure rendezvous for all these edge devices and the HMI & historian cloud services via connections between the cloud services. All communications would be via HTTPS, SOAP and higher-level application abstractions.
This vision makes sense for some applications and possibly even some entire industries but makes less sense for others. For example, would the public be comfortable flying on an aircraft when the jet engines have Internet connections? This would let every hacker or nation-state adversary on the planet send attack packets to all flight long testing for zero-day vulnerabilities. Would industries and governments be content to have the PLCs controlling half-billion-dollar steam turbines routable to & from the Internet and so open to constant attack attempts?
OT Zero Trust
Practically speaking, most industrial control system components are implemented in ways that make this debateable IIoT vision impractical. Many low-level devices and even intermediate-level or high-level systems still use un-encrypted, unauthenticated protocols. Most engineering teams are absolutely not willing to connect safety systems, protective relays or even commonplace PLCs directly on the Internet, no matter how those systems might be encrypted, authenticated or otherwise software-hardened, now or in the future. Government advice, such as the recent NSA and CISA Alert AA20-205A still strongly urges owners and operators not to connect OT equipment directly to the Internet, and to avoid so much as connecting such equipment directly to IT networks.
First steps towards OT zero trust use zero trust concepts and technology in different ways:
- Enable and use zero-trust / HTTPS / authentication technologies within ICS networks whenever such use is practical and does not conflict with essential safety and reliability imperatives, and
- Model the entire OT network as a network segment, or microsegment, and manage connections between that segment and external services using zero trust. When further segmentation is possible and practical, model the OT network internally as multiple microsegments, each with zero-trust-style connections to other microsegments.
The most obvious external manifestation of such designs is that all connections to or via the IT/OT interface are encrypted and authenticated, and almost all are via HTTPS. Such designs are generally practical today for sites able to upgrade their highest-level systems to modern versions. This is because most modern OT components that are designed to communicate with IT systems have at least an option of using HTTPS and PKI.
Unidirectional Zero Trust
These are only “baby steps” towards zero trust, however. This is because modern attacks routinely pivot. For example, an attacker might exploit a known vulnerability or a zero-day vulnerability in cryptosystems or communications drivers in an IT-facing or Internet-facing “zero trust” OT system, and then use this compromised system to extend the attack deeper into OT systems.
Secure industrial sites do not rely on software protections alone, but deploy unidirectional zero-trust systems. In this design, the IT/OT firewall is augmented or replaced by a Unidirectional Security Gateway. The gateway replicates edge devices and industrial servers, such as OPC-UA and historian servers, to the IT network. Enterprise network users and applications that need industrial data establish normal, zero-trust connections to the replica servers and devices. As a result, unidirectional zero-trust designs participate naturally in enterprise networks, so much so that enterprise users generally have on idea that unidirectional protections have been deployed.
Attackers notice though. No matter what credentials they steal, or certificates they forge, or zero-day vulnerabilities those attackers exploit, no network-based attack can penetrate a Unidirectional Gateway to put OT networks at risk. This is because the gateway hardware is physically able to send information in only one direction, from the OT microsegment out to the enterprise network, or straight out to Internet and cloud-based services if necessary.
Future-Proof OT Security


In a world where both threats and connectivity are increasing steadily, a unidirectional zero trust design for OT networks provides important benefits:
- unidirectional zero-trust interoperates seamlessly with zero-trust Internet-based and enterprise systems,
- unidirectional systems provide the strongest possible network protections for reliability-critical OT networks,
- unidirectional zero-trust designs meet or exceed OT security regulations, standards and best practices, including NERC CIP, NIST 800-82 and the NIST Cybersecurity Framework.
Zero-trust is emerging as the modern, natural way for applications and systems to work together. Unidirectional zero trust is the strongest practical way to enjoy zero trust benefits for OT networks.
Ot Solutions Laptops For Windows 10
- Top 10 Targeted Ransomware Attacks of 2020 | The Industrial Security Institute - February 12, 2021
- Help Net Security Article: Misplaced expectations securing water treatment systems - February 10, 2021
- eBook: ICS/OT Ransomware in the Supply Chain: Learnings from attacks in 2020 - February 10, 2021